
- Introduction to Encryption and Decryption
- Symmetric Encryption
- Asymmetric Encryption
- Hashing
- Salting and Its Importance
- Initialization Vectors (IVs) in Encryption
- Comparative Analysis and Use Cases
- Practical Examples in Python
- Symmetric Encryption with AES
- Asymmetric Encryption with RSA
- Hashing with SHA-256
- Adding Salts to Hashes
Introduction to Encryption and Decryption
In the modern IT world understanding Encryption, Decryption and Hashing is as important as to know how to breathe. They are fundamental concepts in the realm of digital security. Encryption refers to the process of converting plain text or data into a coded format, rendering it unreadable to unauthorized users. This transformation is achieved through the use of algorithms and cryptographic keys, ensuring that sensitive information remains confidential during transmission or storage.
The importance of encryption cannot be overstated, particularly in today’s digital age where cyber threats are becoming increasingly sophisticated. Encryption serves as a critical safeguard against data breaches, identity theft, and various forms of cyber-attacks. By encrypting data, individuals and organizations can protect their proprietary information, financial records, and personal communications from being intercepted or accessed by malicious actors.
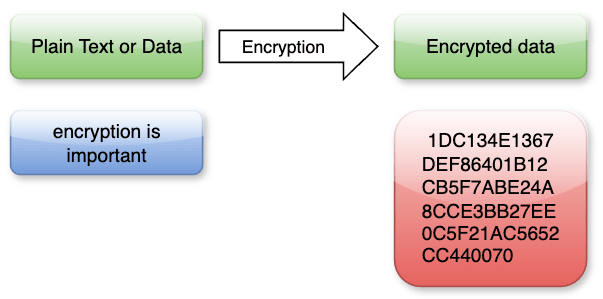
Decryption, on the other hand, is the process of converting the encrypted data back into its original form. This is accomplished using a decryption key, which is usually known only to the intended recipient or authorized users. Decryption ensures that the encoded information can be accurately and securely accessed when needed, maintaining the integrity and confidentiality of the data.
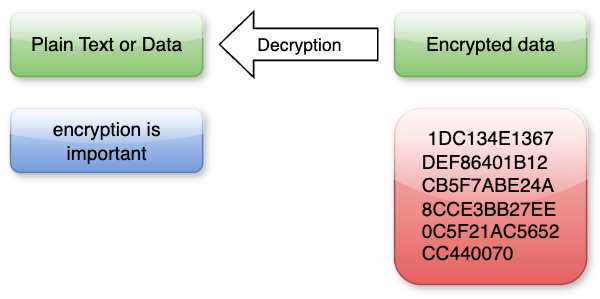
In the context of the digital world, encryption and decryption are indispensable tools for ensuring privacy and security. From securing online transactions and communications to protecting sensitive government and corporate data, the applications of these processes are vast and varied. As cyber threats continue to evolve, the relevance of robust encryption and decryption mechanisms becomes ever more critical, providing a necessary defense in the ongoing battle against cybercrime.
Symmetric Encryption
Symmetric encryption is a method where the same key is utilized for both the encryption and decryption processes. This approach is straightforward and efficient, making it a popular choice for various applications that require secure data storage and transmission. The primary mechanism involves converting plaintext into ciphertext using a specific algorithm and a secret key. The same key is then applied in reverse to transform the ciphertext back into its original form.
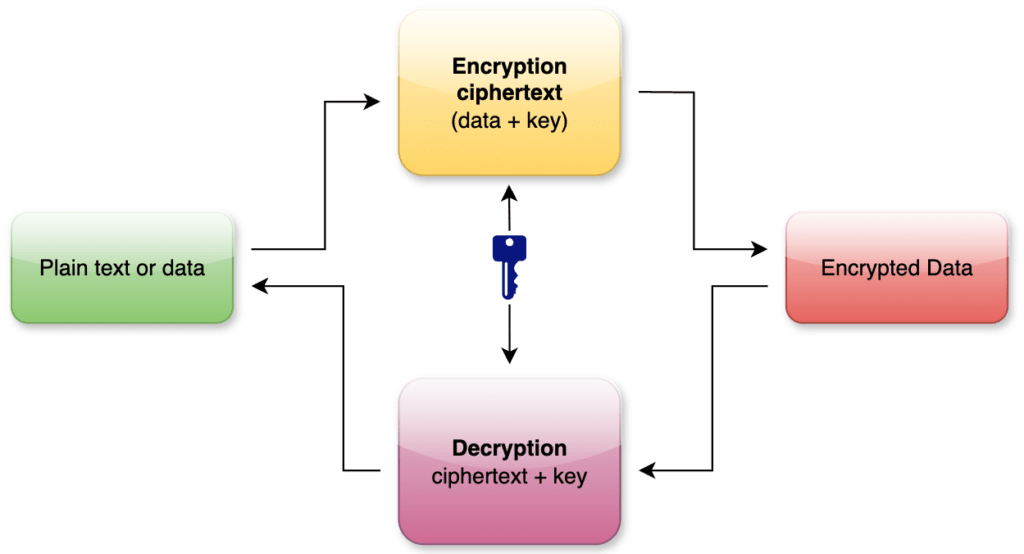
One of the main advantages of symmetric encryption lies in its simplicity and speed. Because the algorithms are generally less complex than their asymmetric counterparts, they require less computational power, resulting in faster processing times. This efficiency makes symmetric encryption suitable for encrypting large volumes of data, such as securing files on a hard drive or protecting data transmitted over networks.
However, symmetric encryption also has notable drawbacks. The most significant challenge is key distribution. Since both parties need access to the same secret key, securely sharing this key can be problematic, especially over unsecured channels. If the key is intercepted or compromised, the encrypted data becomes vulnerable to unauthorized access.
To illustrate the application of symmetric encryption, consider the Advanced Encryption Standard (AES) and the Data Encryption Standard (DES). AES is widely regarded for its robustness and efficiency, making it a standard for securing sensitive data. It supports multiple key lengths (128, 192, and 256 bits), providing flexibility and enhanced security. DES, though once a standard, has become less favorable due to its shorter key length (56 bits), which makes it more susceptible to brute-force attacks.
In practical scenarios, symmetric encryption is often used in conjunction with other security measures to enhance overall data protection. For instance, it’s commonly employed in securing file storage, where files are encrypted before being saved on a disk, ensuring that unauthorized users cannot access the data even if they gain physical access to the storage medium. Similarly, symmetric encryption is utilized for secure data transmission, ensuring that information sent over the internet remains confidential.
Asymmetric Encryption
Asymmetric encryption, also known as public-key cryptography, is a method where two different keys are used for encryption and decryption. These keys are known as the public key and the private key. The public key is accessible to anyone, while the private key is kept confidential by the owner. This dual-key system enhances security by ensuring that even if the public key is widely distributed, the encrypted data remains secure unless the private key is compromised.
The working mechanism of asymmetric encryption begins with the generation of a key pair. This process involves complex mathematical algorithms that create two interdependent keys. When a sender wants to transmit confidential information, they use the recipient’s public key to encrypt the data. Once encrypted, the data can only be decrypted by the corresponding private key, ensuring that only the intended recipient can access the information. See image below (green is the public key, dark blue is the private key). In this context anyone with a public key can encrypt a message but only those who have the corresponding private key (from here the key pair) can decrypt the ciphertext for getting the original set of data.
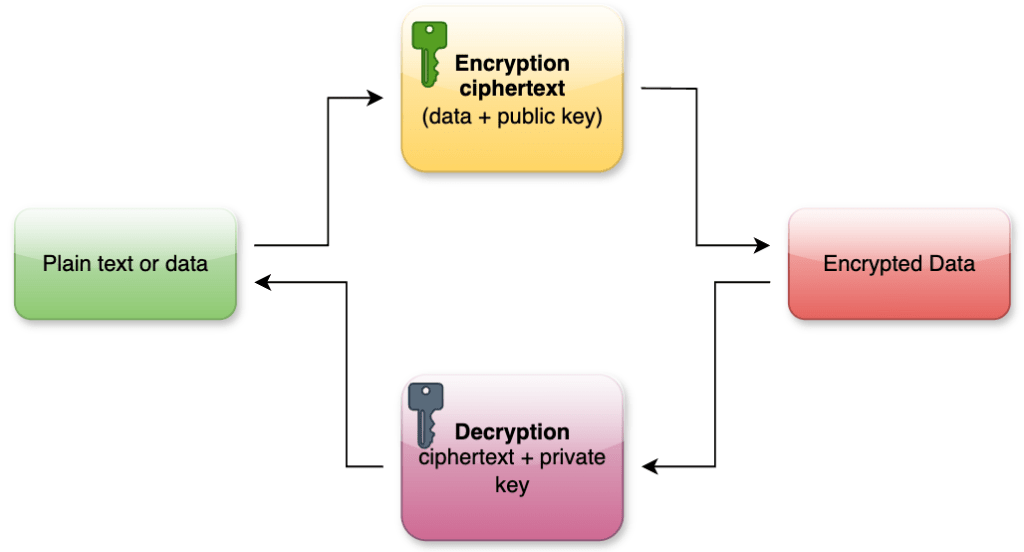
One of the significant advantages of asymmetric encryption over symmetric encryption is the enhanced security in key distribution. In symmetric encryption, the same key is used for both encryption and decryption, necessitating secure channels for key exchange. Asymmetric encryption eliminates this issue by allowing public keys to be openly shared without compromising security, as the private key remains private and secure.
Asymmetric encryption is widely used in various practical applications. For instance, SSL/TLS protocols utilize asymmetric encryption to secure web communications, ensuring that data transmitted between a user’s browser and a website remains confidential. Email encryption is another common application, where public keys are used to encrypt emails, and private keys are used to decrypt them, maintaining the privacy of email communications.
Several common algorithms are employed in asymmetric encryption, with RSA (Rivest-Shamir-Adleman) and ECC (Elliptic Curve Cryptography) being among the most prevalent. RSA relies on the mathematical properties of large prime numbers, making it highly secure but computationally intensive. ECC, on the other hand, offers similar security levels with smaller key sizes, resulting in faster computations and reduced resource requirements. These algorithms form the backbone of modern asymmetric encryption, providing robust security for a wide range of applications.
Hashing
Hashing plays a critical role in ensuring data integrity within the realm of encryption and decryption. Hashing is a process that converts data of any size into a fixed-size hash value, commonly referred to as a hash code or digest. This transformation is accomplished using a hash function, which is designed to be a one-way function, meaning the original data cannot be feasibly reversed or retrieved from the hash value. Due to this property, hashing is extensively employed in various security applications.
One of the primary uses of hashing is in securely storing passwords. Instead of storing plain text passwords, systems store the hashed version of the password. When a user attempts to log in, the system hashes the entered password and compares it to the stored hash. If the hashes match, the authentication is successful, ensuring that even if the password database is compromised, the actual passwords remain protected.

Hashing is also crucial in verifying data integrity. By generating a hash value of a file or message, one can ensure that the content has not been altered during transmission. The recipient can generate a hash value on their end and compare it to the original hash value; any discrepancy indicates possible tampering. Additionally, digital signatures rely on hashing to verify the authenticity and integrity of messages or documents.
Several hashing algorithms are in common use, each with its strengths and applications. SHA-256 (Secure Hash Algorithm 256-bit) is widely used due to its strong security properties, making it a popular choice in blockchain technology and digital certificates. MD5 (Message-Digest Algorithm 5), though once prevalent, is now considered less secure due to vulnerabilities and is generally avoided in favor of more robust alternatives.
To illustrate hashing in practice, consider the following Python example using the hashlib library:
import hashlib
datadata = "Understanding Encryption and Decryption"
# Generate SHA-256
hashsha256_hash = hashlib.sha256(data.encode()).hexdigest()
print(f"SHA-256: {sha256_hash}")
# Generate MD5
hashmd5_hash = hashlib.md5(data.encode()).hexdigest()
print(f"MD5: {md5_hash}")This simple script demonstrates how to generate SHA-256 and MD5 hashes for a given piece of data, highlighting the ease with which hashing can be implemented in software development. By understanding and utilizing hashing, one can enhance the security and integrity of data across various applications.
Salting and Its Importance
Salting is a critical process in the realm of encryption and decryption, involving the addition of random data to the input of a hash function to produce unique hash values. This technique is particularly crucial in enhancing the security of hashed data, making it significantly more resilient against various types of attacks, especially rainbow table attacks.
In the context of password storage and authentication systems, salting plays a pivotal role. When a password is hashed, the resulting hash value can be vulnerable to precomputed attacks, like those using rainbow tables. A rainbow table is a precomputed table for reversing cryptographic hash functions, primarily used for cracking password hashes. By adding a unique salt to each password before hashing, even identical passwords will produce different hash values, thus rendering rainbow tables ineffective.
To illustrate, consider two users with the same password. Without salting, both passwords would produce the same hash, making it easier for attackers to exploit this uniformity. However, by introducing a unique salt for each user, the resultant hashes become distinct, significantly bolstering security. For example, if user A’s password “password123” is salted with “xyz123” and user B’s with “abc456,” the two salted and hashed passwords will be entirely different.
Best practices for generating and storing salts recommend that salts be long enough to thwart precomputed lookup attacks and randomly generated to ensure uniqueness. Typically, a salt length of at least 16 bytes is considered sufficient. Moreover, it is essential to store the salt alongside the hashed password securely. Modern cryptographic libraries and algorithms often provide built-in support for salting, ensuring robust implementation.
In conclusion, salting is an indispensable practice in modern cryptographic systems, enhancing the security of stored passwords and other sensitive data. By ensuring that each hash is unique, salting prevents attackers from leveraging precomputed tables and other methods to compromise security, making it a cornerstone in the field of cryptography.
Initialization Vectors (IVs) in Encryption
Initialization Vectors (IVs) play a pivotal role in the encryption process, particularly in block cipher modes such as Cipher Block Chaining (CBC). These vectors are essential for ensuring that identical plaintext blocks produce distinct ciphertexts, thereby enhancing the overall security of the encryption mechanism. Without the use of IVs, identical plaintext inputs would result in identical ciphertext outputs, making it easier for potential attackers to detect patterns and compromise the encrypted data.
IVs are typically random or pseudo-random values that are combined with the plaintext before the encryption process begins. In the CBC mode, for example, the IV is XORed with the first block of plaintext before encryption. This ensures that even if the same plaintext is encrypted multiple times, the resulting ciphertext will differ, provided that a unique IV is used for each encryption operation. The use of IVs effectively adds an additional layer of randomness, making it significantly more difficult for adversaries to decrypt the data without the appropriate keys and IVs.
In practice, IVs can be generated using various methods, including hardware-based random number generators or software-based algorithms designed to produce high-entropy values. It’s crucial that IVs are unique for each encryption operation; reusing IVs can severely compromise the security of the encrypted data. For instance, if the same IV is used for encrypting multiple blocks of plaintext, the resulting ciphertexts may reveal patterns that could be exploited by malicious actors.
To illustrate, consider an encryption system that uses CBC mode. When encrypting a document, a random IV is generated and combined with the first block of plaintext. This combination is then encrypted to produce the first block of ciphertext. The same process is repeated for subsequent blocks, with each block of plaintext being XORed with the previous block of ciphertext before encryption. This chaining mechanism, facilitated by the IV, ensures that each block of ciphertext is dependent on both the current and previous plaintext blocks, thereby enhancing security.
In conclusion, the use of Initialization Vectors in encryption is a fundamental aspect of ensuring data security. By introducing randomness and uniqueness into the encryption process, IVs help prevent the exposure of patterns that could be exploited by attackers. It is imperative for encryption systems to generate and utilize unique IVs for each encryption operation to maintain the integrity and confidentiality of the encrypted data.
Comparative Analysis and Use Cases
Encryption and decryption are critical components of data security, each serving unique purposes and fitting distinct use cases. Broadly, they can be categorized into symmetric encryption, asymmetric encryption, hashing, and salting. Understanding the benefits and limitations of each method aids in selecting the appropriate technique for specific applications.
Symmetric encryption involves the use of a single key for both encryption and decryption. This method is known for its efficiency and speed, making it ideal for encrypting large volumes of data. However, the primary limitation lies in key distribution; securely sharing the key between parties can be challenging. A common use case for symmetric encryption is in securing data at rest, such as encrypting files stored on a hard drive, where the key can be managed locally.
Asymmetric encryption, on the other hand, uses a pair of keys – a public key for encryption and a private key for decryption. This method excels in secure key exchange and is widely used in secure communications. The major drawback is its computational intensity, which makes it slower than symmetric encryption. Practical applications include SSL/TLS for securing web traffic, where the server’s public key encrypts data sent by the client, and the server’s private key decrypts it.
Hashing transforms data into a fixed-size string of characters, which is typically a hash value. Hashing is crucial for data integrity verification and password storage. Its one-way nature means that once data is hashed, it cannot be reversed to retrieve the original data, ensuring security. A common use case is in verifying file integrity; for instance, downloading software and validating its hash value against the provided checksum to ensure it hasn’t been tampered with.
Salting is often paired with hashing to enhance security by adding random data to the input of a hash function. This prevents attackers from using precomputed tables (rainbow tables) to crack hashed passwords. Salting is particularly beneficial in authentication systems, where it ensures that even if two users have the same password, their hashed passwords will be unique.
Each of these techniques plays a vital role in different contexts. For instance, a secure messaging app might use asymmetric encryption for key exchange and symmetric encryption for the actual message content, ensuring both security and efficiency. In data storage, hashing and salting are indispensable for protecting user passwords. By understanding the strengths and limitations of each method, organizations can implement robust security measures tailored to their specific needs.
Practical Examples in Python
Encryption and decryption are fundamental concepts in securing data. Let’s explore practical examples of implementing these techniques using Python. We’ll cover symmetric encryption with AES, asymmetric encryption with RSA, hashing with SHA-256, and adding salts to hashes.
Symmetric Encryption with AES
Symmetric encryption uses the same key for both encryption and decryption. The Advanced Encryption Standard (AES) is a widely used algorithm for this purpose. Below is a Python example using the `pycryptodome` library:
from Crypto.Cipher import AES
from Crypto.Random import get_random_bytes
def encrypt_AES_GCM(key, data):
# Create cipher object and encrypt the data
cipher = AES.new(key, AES.MODE_GCM)
ciphertext, tag = cipher.encrypt_and_digest(data)
return cipher.nonce, ciphertext, tag
def decrypt_AES_GCM(key, nonce, ciphertext, tag):
# Create cipher object and decrypt the data
cipher = AES.new(key, AES.MODE_GCM, nonce=nonce)
data = cipher.decrypt_and_verify(ciphertext, tag)
return data
# Example usage
key = get_random_bytes(16) # AES key must be either 16, 24, or 32 bytes long
data = b"This is a secret message."
# Encrypt the data
nonce, ciphertext, tag = encrypt_AES_GCM(key, data)
print(f"Nonce: {nonce.hex()}")
print(f"Ciphertext: {ciphertext.hex()}")
print(f"Tag: {tag.hex()}")
# Decrypt the data
decrypted_data = decrypt_AES_GCM(key, nonce, ciphertext, tag)
print(f"Decrypted data: {decrypted_data.decode('utf-8')}")Explanation:
- Import Libraries: Import the necessary functions from the
PyCryptodomelibrary. - Encrypt Function:
AES.new(key, AES.MODE_GCM): Create a new AES cipher object in GCM mode.cipher.encrypt_and_digest(data): Encrypt the data and generate an authentication tag.- The function returns the nonce, the ciphertext, and the authentication tag.
- Decrypt Function:
AES.new(key, AES.MODE_GCM, nonce=nonce): Create a new AES cipher object in GCM mode using the provided nonce.cipher.decrypt_and_verify(ciphertext, tag): Decrypt the data and verify the authentication tag.- The function returns the decrypted data.
- Example Usage:
- Generate a random AES key of 16 bytes.
- Define the data to be encrypted.
- Encrypt the data and print the nonce, ciphertext, and tag in hexadecimal format.
- Decrypt the data and print the original message.
Asymmetric Encryption with RSA
Asymmetric encryption uses a pair of keys: a public key for encryption and a private key for decryption. Here is a Python example using the `PyCryptodome` library:
from Crypto.PublicKey import RSA
from Crypto.Cipher import PKCS1_OAEP
from Crypto.Random import get_random_bytes
def generate_keys():
# Generate RSA keys
key = RSA.generate(2048)
private_key = key.export_key()
public_key = key.publickey().export_key()
return private_key, public_key
def encrypt_RSA(public_key, data):
# Load the public key and encrypt the data
recipient_key = RSA.import_key(public_key)
cipher_rsa = PKCS1_OAEP.new(recipient_key)
encrypted_data = cipher_rsa.encrypt(data)
return encrypted_data
def decrypt_RSA(private_key, encrypted_data):
# Load the private key and decrypt the data
private_key = RSA.import_key(private_key)
cipher_rsa = PKCS1_OAEP.new(private_key)
decrypted_data = cipher_rsa.decrypt(encrypted_data)
return decrypted_data
# Example usage
private_key, public_key = generate_keys()
# Print keys in PEM format
print(f"Private Key:\n{private_key.decode('utf-8')}")
print(f"Public Key:\n{public_key.decode('utf-8')}")
data = b"This is a secret message."
# Encrypt the data with the public key
encrypted_data = encrypt_RSA(public_key, data)
print(f"Encrypted data: {encrypted_data.hex()}")
# Decrypt the data with the private key
decrypted_data = decrypt_RSA(private_key, encrypted_data)
print(f"Decrypted data: {decrypted_data.decode('utf-8')}")
Hashing with SHA-256
Hashing converts data into a fixed-size string of characters, which is typically a digest that is unique to each unique input. Here’s an example using Python’s `hashlib` library:
import hashlib
def hash_message(message):
# Create a new SHA-256 hash object
sha256_hash = hashlib.sha256()
# Update the hash object with the bytes-like object (message)
sha256_hash.update(message)
# Get the hexadecimal representation of the digest
hashed_message = sha256_hash.hexdigest()
return hashed_message
# Example usage
message = b"Hello, this is a message to hash using SHA-256!"
hashed_message = hash_message(message)
print(f"Original message: {message.decode('utf-8')}")
print(f"SHA-256 hash: {hashed_message}")
Explanation:
- Import
hashlib: Import thehashliblibrary which provides the SHA-256 hashing algorithm. - Hash Message Function:
hashlib.sha256(): Create a new SHA-256 hash object.sha256_hash.update(message): Update the hash object with the message. The message must be a bytes-like object, hence thebprefix for the string.sha256_hash.hexdigest(): Get the hexadecimal representation of the hash digest.
- Example Usage:
- Define the message to be hashed. The message is a bytes object.
- Call the
hash_messagefunction with the message. - Print the original message and its SHA-256 hash.
Adding Salts to Hashes
Salting enhances the security of hashed passwords by adding a random value (salt) before hashing. Here is an example:
In this example, we generate a random salt, concatenate it with the data, and then hash the combination. The salt is stored along with the hash to verify the data later.
import hashlib
import os
def hash_message_with_salt(message, salt=None):
if salt is None:
# Generate a random salt
salt = os.urandom(16) # 16 bytes = 128 bits
# Create a new SHA-256 hash object
sha256_hash = hashlib.sha256()
# Update the hash object with the salt and message
sha256_hash.update(salt + message)
# Get the hexadecimal representation of the digest
hashed_message = sha256_hash.hexdigest()
return salt, hashed_message
# Example usage
message = b"Hello, this is a message to hash using SHA-256 with salt!"
salt, hashed_message = hash_message_with_salt(message)
print(f"Original message: {message.decode('utf-8')}")
print(f"Salt: {salt.hex()}")
print(f"SHA-256 hash with salt: {hashed_message}")
By understanding these practical examples, you can implement encryption, decryption, hashing, and salting in your Python projects to enhance data security.
Share this content:
